What do ancient Egyptians and Julius Caesar have in common? They were some of the earliest users of encryption to convert messages with sensitive information “into a form unreadable by anyone except the intended recipient.”
Around 1900 BC there is evidence of Egyptians using cryptography in hieroglyphs. Caesar’s encryption was pretty basic; he took the alphabet and “shifted by 3” so each “A” in his message was replaced by a “D” while each “B” was replaced with an “E,” etc.
One of the most famous uses of encryption came during WWII. The encryption key for the Enigma machine used by Germany during WWII was reset everyday at midnight, which gave codebreakers less than 20 hours (from the time messages were intercepted) to attempt to crack the code before being forced to start from scratch.
Encryption methods have become more complex with technology advancements, and you and I can thank sophisticated encryption processes for allowing us to make secure purchases in a digital economy.
However, in today’s world of online payment processing and recurring billing, tokenization has replaced encryption as the preferred method of protecting sensitive credit card data. The word is thrown around frequently, but many people are pretty hazy on what tokenization actually is. We’ve got you covered. In today’s blog we’re explaining the basics of tokenization:
- What exactly is tokenization
- How tokenization differs from encryption
- How tokenization works
- Why it matters
What is tokenization?
Tokenization protects sensitive data by replacing the information with a unique digital identifier (the “token”). Tokens can be used to replace a variety of data ranging from medical information to clearing house data, but the most popular use of tokenization is to securely protect credit card data.
Once a token is created it can be used for payment without exposing the original credit card information. By themselves, tokens have no real meaning—they’re just a random string of numbers and/or characters. The tokenized numbers are randomly generated, making it is almost impossible to mathematically reverse-engineer the tokens to get the original credit card data.

What’s the difference between tokenization and encryption?
“Encryption is the transformation of data into a form unreadable by anyone without a secret decryption key,” according to Stanford computer science professor Eric Roberts.
Unlike tokenization, sensitive data protected by encryption is mathematically reversible:
Due to the increased security offered, the majority of payment gateways now utilize tokenization to secure sensitive credit card data. Note: All of the payment gateways Maxio integrates with use tokenization to protect your subscribers’ credit card information.
How does tokenization work?
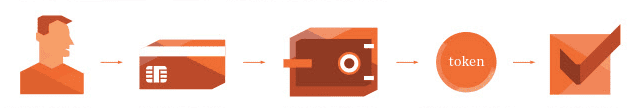
- A subscriber signs up and enters their credit card information.
- The credit card data passes to the payment gateway which authenticates the request and processes the payment.
- The credit card data is stored in the payment gateway’s vault and a vault token for the credit card data is assigned.
- The payment gateway passes the vault token back to Maxio (or the initial site where the signup occurred, if you aren’t using a recurring billing platform).
- Maxio attaches the token information to the correlated subscription.
Why does it matter?
Security: Security is paramount to subscribers and business owners. Subscription-based businesses, in which a subscriber’s credit card is “put on file” for recurring billing, benefit greatly from the increased security and fraud protection tokenization provides.
Don’t forget mobile. Tokenization “provides a secure method for enabling payments through mobile wallets and near-field communication (NFC),” says Fiserv’s Allison Edwards.
For your customers, tokens allow their credit card information to be stored and recharged without exposing the original card information.
It is important to note that employing tokenization does not automatically make a merchant PCI compliant. If you’re using Maxio(shameless plug), we’ve got you covered; Maxio is a Level 1 PCI compliant service provider.
Convenience: Tokens are convenient for you and your customers. You don’t have to worry about sensitive data passing through your own systems.
As your customers “increasingly shop with connected devices, the need for a seamless and secure digital payment experience becomes crucial. Without exposing the consumer’s account to fraud, tokenization enables frictionless, card-free payments in digital commerce environments,” according to Visa.
Switching payment gateways: As we mentioned previously, the majority of payment gateways (and certainly all of the major gateways) utilize tokenization. But, each payment gateway’s vault tokens have their own syntax. Which means that if you want to switch payment gateways, the vault tokens for your subscribers will need to be “re-mapped.” The process by which this is done (and the difficulty level of the re-mapping) is unique to each payment gateway, but it may be one of the points to consider when selecting a payment gateway.
Wrap-up
While the goal of protecting sensitive data is the same for both, encryption and tokenization remain two different technologies. As a subscription-based business, it is helpful to have a basic understanding of how tokenization protects your business and customers. All major payment gateways have adapted tokenization and utilize vault tokens to provide merchants with more security and fraud protection.